Set Up AD Domain Over VPN
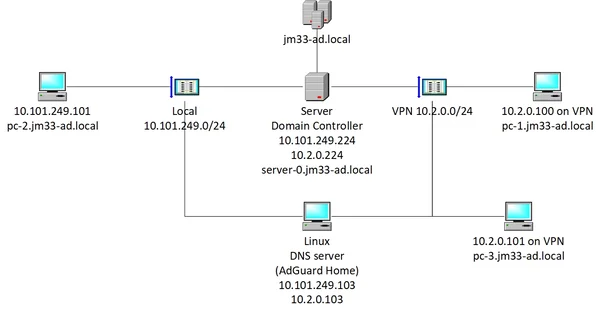
this is the setup of my AD domain:
install Active Directory Domain Services (AD DS)
install using server manager
assuming you are using Windows Server 2012 or later, in the server manager window, click Manage -> Add roles and features
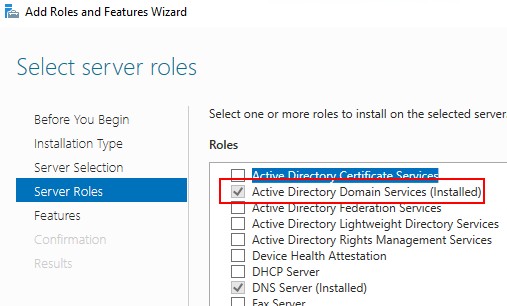
DNS Server will be installed as well
i dont want to …
more ...