Migrating from Libvirt to Qemu
Graphics in Qemu
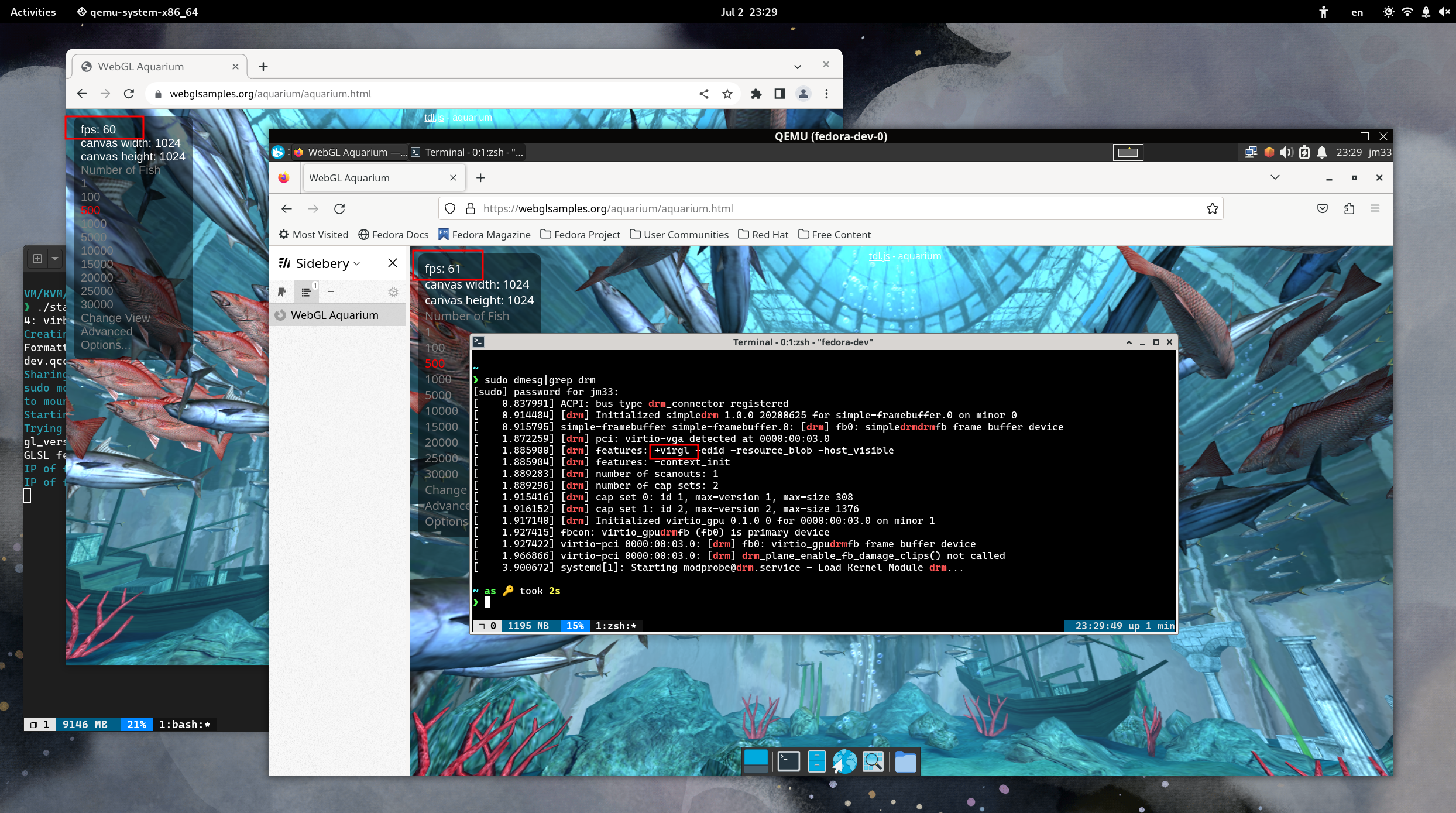
Performance Impact of SPICE+VirGL
I have been using libvirt (virt-manager) for years, until recently I tried to run Linux VMs with Qemu directly using virgl.
Running a Linux VM with Qemu's SDL display is much smoother than SPICE+VirGL solution provided by virt-manager, it made me …
more ...