emp3r0r - 0x02
this part is about reverse shell
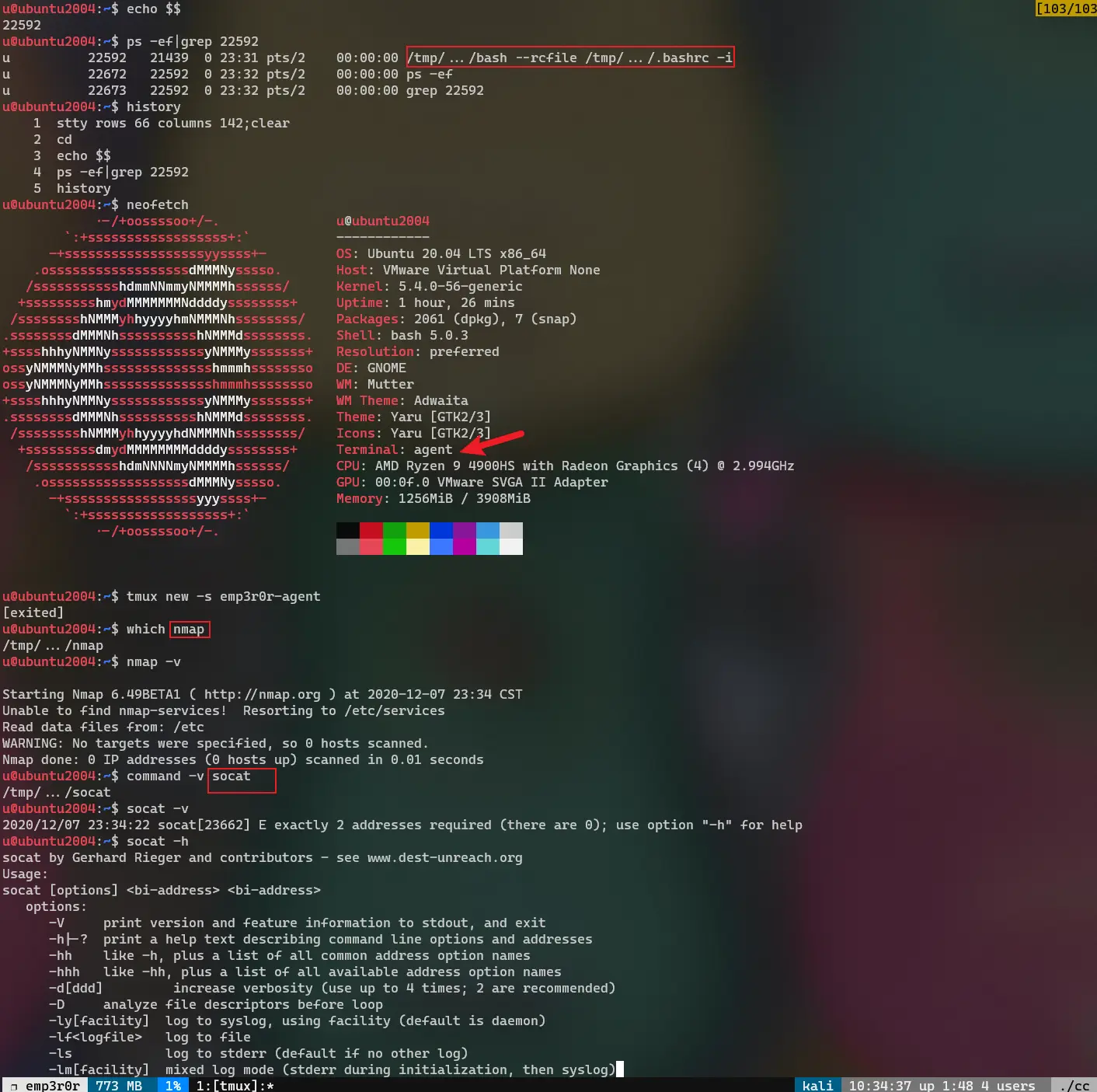
how to make your reverse shell suck less
take a look at pentestmonkey's Reverse Shell Cheat Sheet, which gives you a collection of reverse shell one-liners. each of the one-liners does the same thing -- establish a TCP connection to you, then execute a shell …
more ...