emp3r0r - SSH
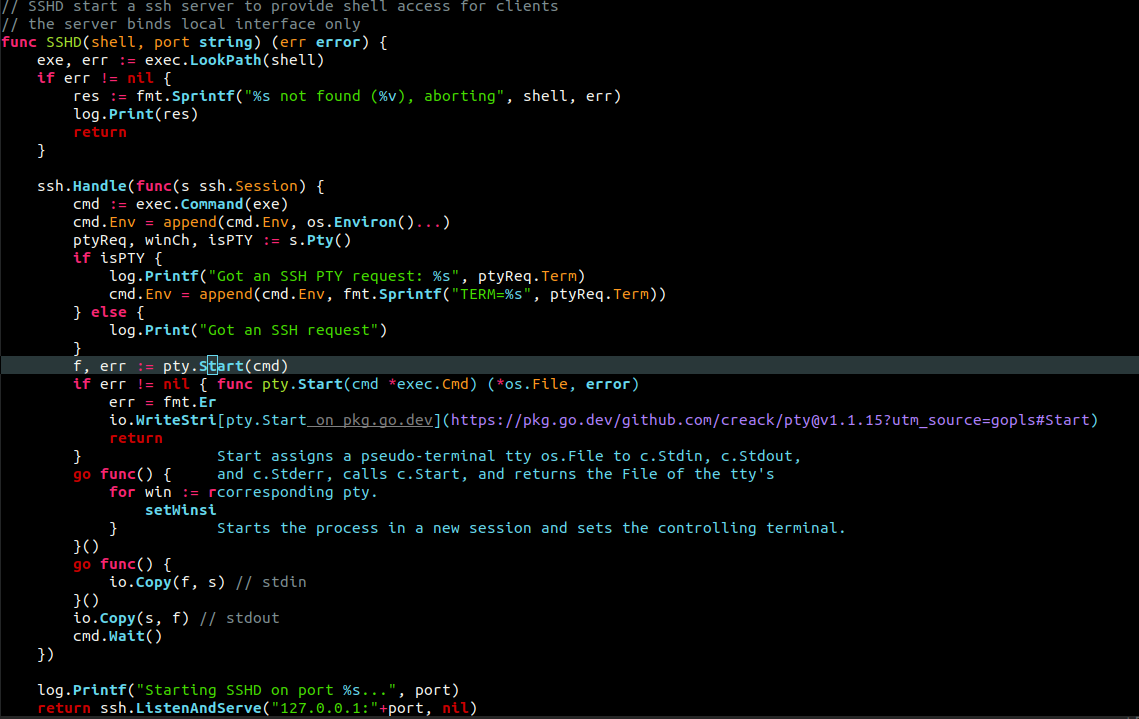
what we can do with ssh
sshto target host for remote shell accesssftpto target host for FTP servicessh -Dfor socks proxyssh -L/ssh -Rfor port mapping
all these features are provided by openssh suite, which we use everyday. why not integrate them into …
more ...