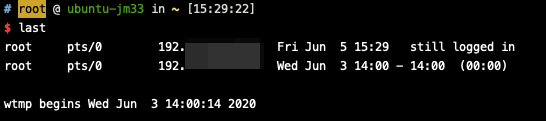
Delete An Entry From wtmp/btmp/utmp Log Files
Stop Deleting Everything!
many folks like to rm -f /var/log/*tmp, which I have to say is not a right way to cover your trail,
if the admin would ever think of checking login logs, an empty log will certainly catch his attention
but *tmp files are all binary …
