About this challenge
-
Instructions
The CTF is a virtual machine and works best in Virtual Box. This OVA was created using Virtual Box 4.3.32. Download the OVA file open up Virtual Box and then select File –> Import Appliance. Choose the OVA file from where you downloaded it. After importing the OVA file above it is best to disable the USB 2.0 setting before booting up the VM. The networking is setup for a NAT Network but you can change this before booting up depending on your networking setup. If you have any questions please send me a message on Twitter @jamesbower and I’ll be happy to help.
- Goal of Sky Dog Con CTF
The purpose of this CTF is to find all six flags hidden throughout the server by hacking network and system services. This can be achieved without hacking the VM file itself.
- Flags
The six flags are in the form of flag{MD5 Hash} such as flag{1a79a4d60de6718e8e5b326e338ae533
Flag #1 Home Sweet Home or (A Picture is Worth a Thousand Words)
Flag #2 When do Androids Learn to Walk?
Flag #3 Who Can You Trust?
Flag #4 Who Doesn’t Love a Good Cocktail Party?
Flag #5 Another Day at the Office
Flag #6 Little Black Box
- PS You may need to disable the USB device in VirtualBox for it to start up.
Walkthrough
Enumeration
- Find your target with
nmap -sn <ip range>
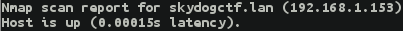
- Go on scanning
nmap -A -Pn 192.168.1.153
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 c8:f7:5b:33:8a:5a:0c:03:bb:6b:af:2d:a9:70:d3:01 (DSA)
| 2048 01:9f:dd:98:ba:be:de:22:4a:48:4b:be:8d:1a:47:f4 (RSA)
|_ 256 f8:a9:65:a5:7c:50:1d:fd:71:57:92:38:8b:ee:8c:0a (ECDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 252 disallowed entries (15 shown)
| /search /sdch /groups /catalogs /catalogues /news /nwshp
| /setnewsprefs? /index.html? /? /?hl=*& /?hl=*&*&gws_rd=ssl
|_/addurl/image? /mail/ /pagead/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
- Fire up nikto to see what's on the web server
nikto -h 192.168.1.153
+ Entry '/index.html?' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?hl=/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?hl=*&/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?hl=*&gws_rd=ssl$/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?hl=*&*&gws_rd=ssl/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?gws_rd=ssl$/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?pt1=true$/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/Setec/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 299 entries which should be manually viewed.
FLAG #1
Home Sweet Home or (A Picture is Worth a Thousand Words)
- I do see a picture on its index.html, the flag must be inside the picture then, let's try with
:%!xxdin vim
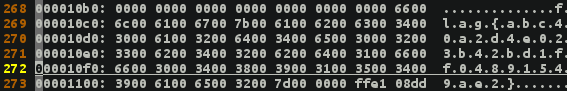
- Go ahead and decrypt this MD5 encrypted string, it will be
Welcome Home
FLAG #2
When do Androids Learn to Walk?
-
Remember
robots.txt? Try to look into it and see if there's anything useful -
Turned out the first line in robots.txt gives us
Congrats Mr. Bishop, your getting good - flag{cd4f10fcba234f0e8b2f60a490c306e6}
cd4f10fcba234f0e8b2f60a490c306e6 MD5 : Bots
FLAG #3
Who Can You Trust?
-
As we saw earlier in nmap, there's one directory called
/Sectecmight be useful to us -
It's more than a picture...
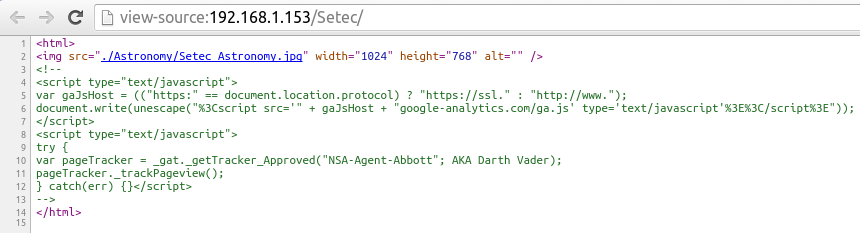
- Try with this
/Astronomy
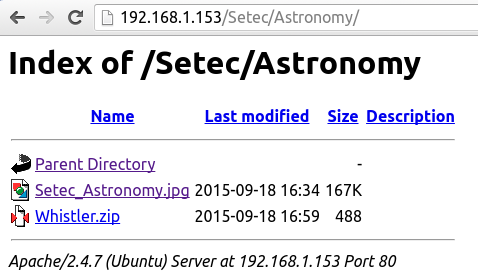
- Now we know where to find our flag, but the zip file is encrypted... Don't worry, just fire up fcrackzip and use the famous
rockyou.txtdictionary, you can find it in Kali Linux(located in/usr/share/wordlists/), the command needed will befcrackzip -D -v -u -p /path/to/dic target.zip
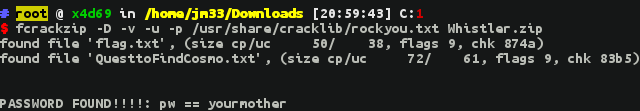
- Here we have our flag #3
flag{1871a3c1da602bf471d3d76cc60cdb9b}
1871a3c1da602bf471d3d76cc60cdb9b MD5 : yourmother
- Also, another file tells us where to look for the flag #4
Time to break out those binoculars and start doing some OSINT
FLAG #4
Who Doesn’t Love a Good Cocktail Party?
- OSINT, which stands or Open Source Intelligence, must has a great deal of connection with the Sectec we found earlier...
var gaJsHost = (("https:" == document.location.protocol) ? "https://ssl." : "http://www.");
document.write(unescape("%3Cscript src='" + gaJsHost + "google-analytics.com/ga.js' type='text/javascript'%3E%3C/script%3E"));
try {
var pageTracker = _gat._getTracker_Approved("NSA-Agent-Abbott"; AKA Darth Vader);
pageTracker._trackPageview();
} catch(err) {}
These two script blocks are commented off(since it does nothing but provide some info for us)
-
NSA-Agent-Abbott(AKA Darth Vader), obviously I haven't watched this movie, as far as I know, I should be looking for a man who played NSA-Agent-Abbott and Darth Vader in Star Wars, let's head to Google then...
-
I found a keywords list on IMDb
TO BE CONTINUED
Comments
comments powered by Disqus