
how do i know
original post here (QQ 正在尝试读取你的浏览记录)
the following content is based on QQ 9.0.4
see what qq does with procmon
i think theres one thing many people tend to ignore, you can view target process's stack snapshot right inside procmon itself, you definitely dont need a debugger to find what you are looking for
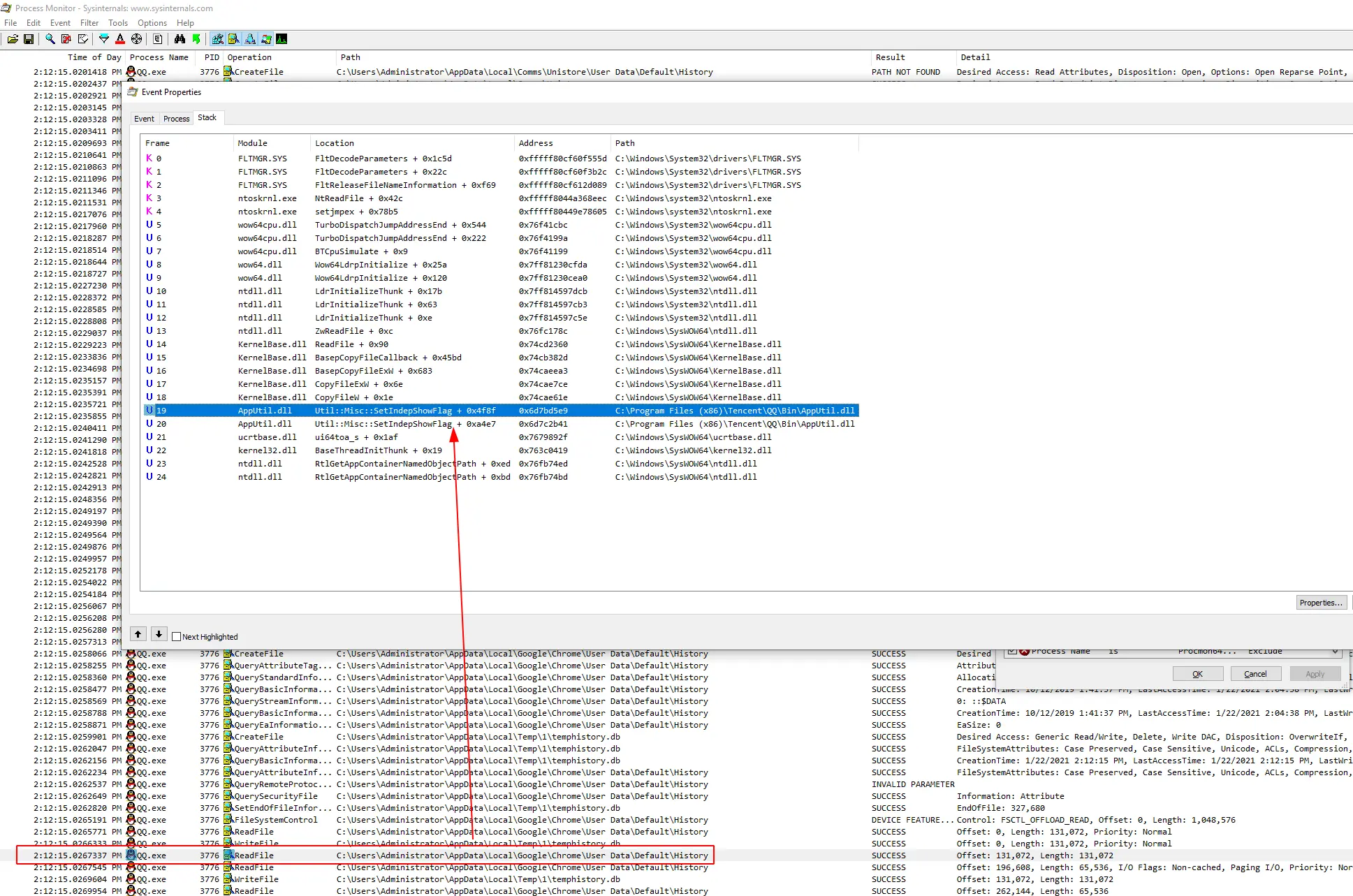
dig into the code
knowing the address of the calling, in Ghidra, press g to jump to that address:
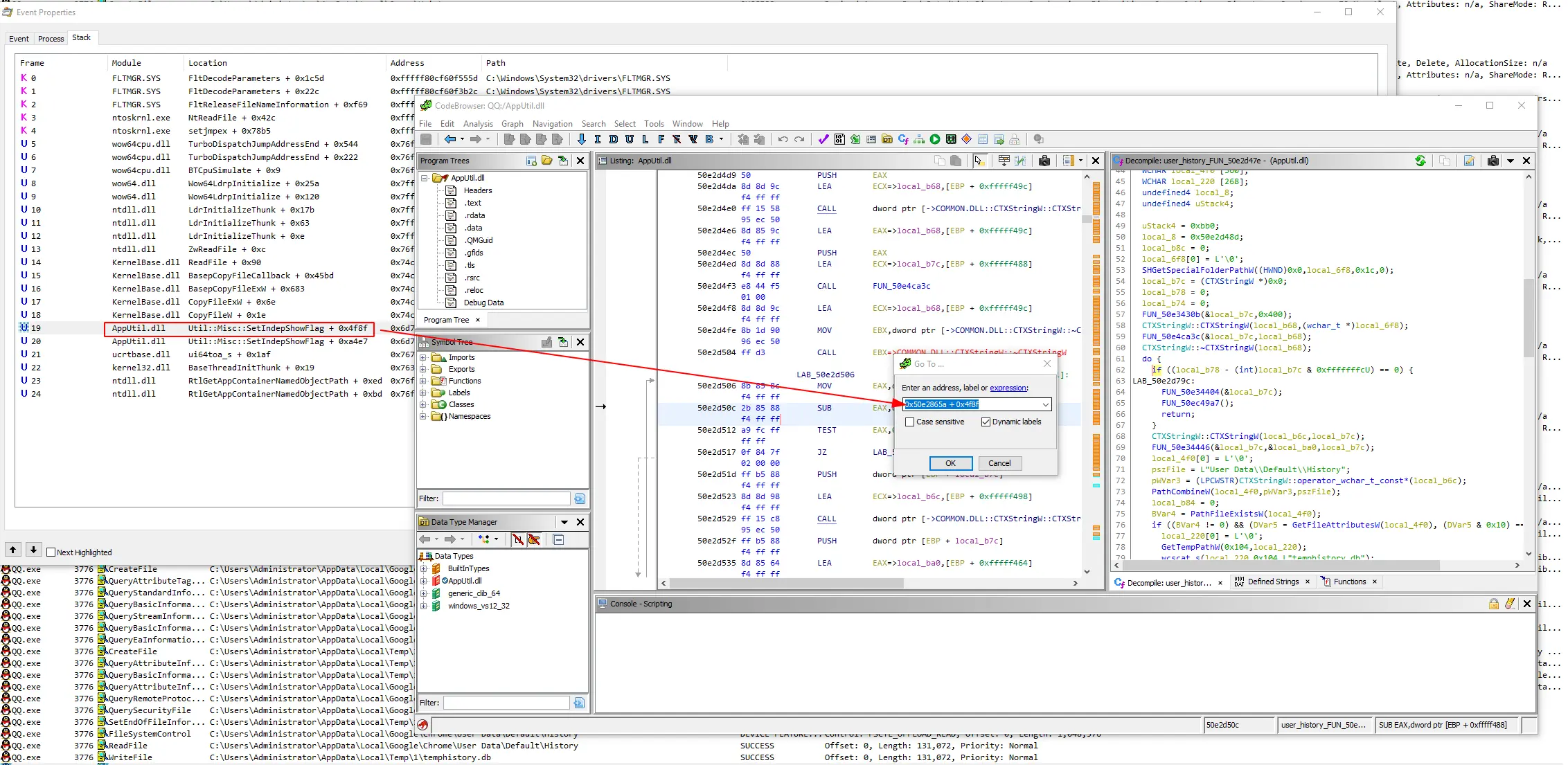
what does it do with my browsing history
the code
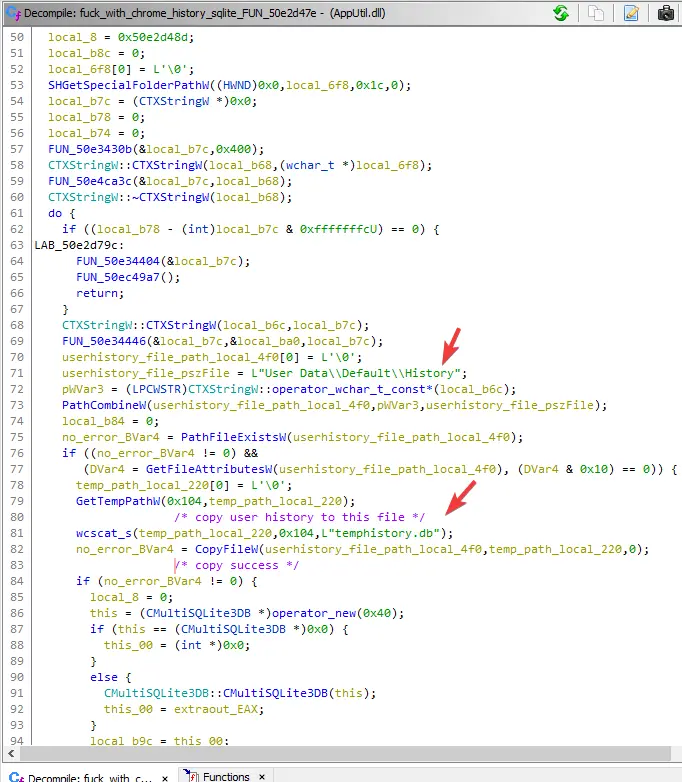
the jump brings us right here, i renamed this function as fuck_with_chrome_history
as you can see in the code, it copies your chrome history which is stored as a SQLite db file to a temporary location, process it, and delete it eventually
here it queries the SQLite db file, in an attempt to find URLs that its interested in
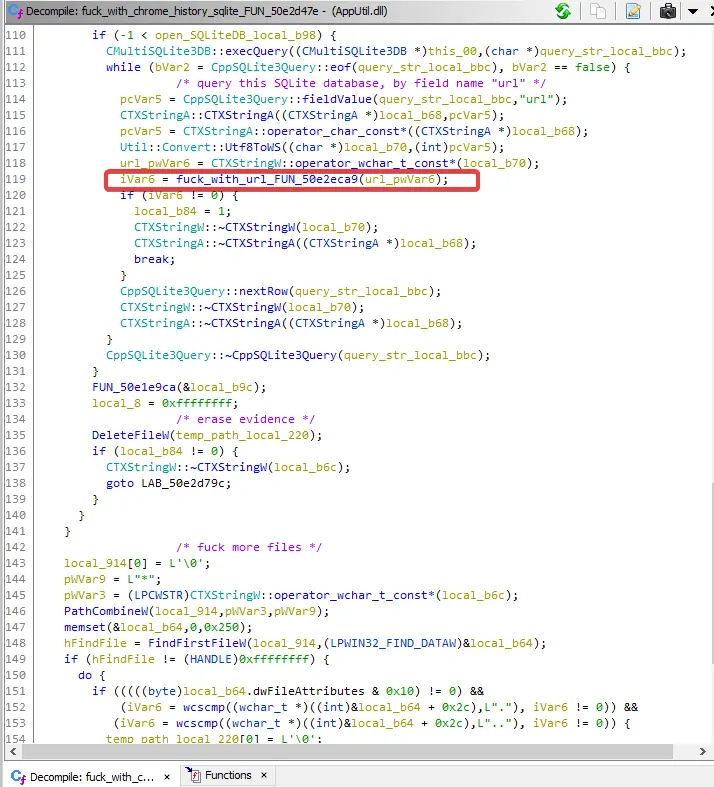
and here is how it fucks your URL:
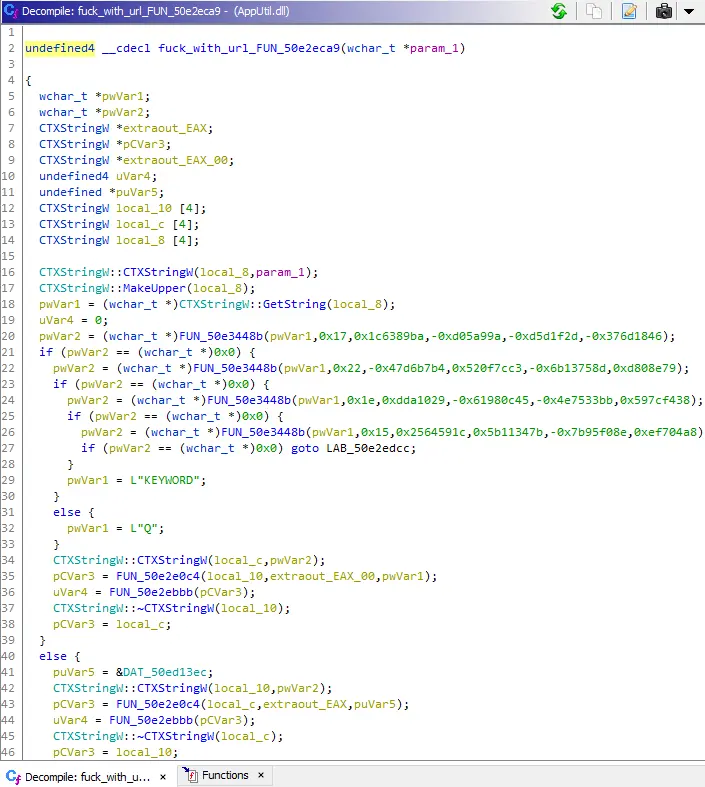
if you want details, please check Jupyter Notebook Viewer, i will add explanation later
some guess
no guess yet, just make your own guess
what can i do about it
if you do care about your privacy, you shouldn't be using such software at all, regardless of what country they are from.
if you have to use them, do put your valuable data away from them
Comments
comments powered by Disqus